Docker Login the Right Way
How to configure a docker-credential-helpers to keep docker credentials safe on Linux

Table of Contents
Docker Login the right Way
Hi again!
It is been a while since I wrote something here, as always, there is no much time for a hobby.
I’ve been working for a while with docker, not a production level, but for some applications that I use at work. And since the Docker Hub Data breach I put more atention on the security of my data/credentials, so I investigate a little about and found this official repository https://github.com/docker/docker-credential-helpers/ from Docker where are the supported credential helpers.
Credential Store
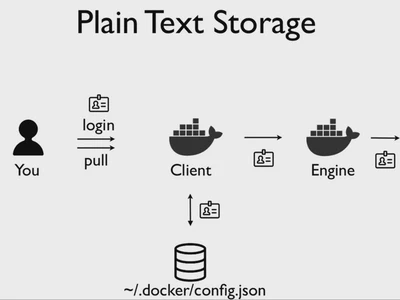
Docker keeps our credentials saved on a JSON file located on ~/.docker/config.json,
but unfortunatelly credentials are just encrypted on base64,
here is an articule/video where there is an explanation for the why it is a bad idea to just use base64 encryption.
The following is a diagram on how a plain text storage works:
Here is an example on how ~/.docker/config.json looks like when is using plain text credentials:
cat ~/.docker/config.json
{
"auths": {
"https://index.docker.io/v1/": {
"auth": "azRjaDA6c3VwZXJzZWNyZXRwYXNzd29yZAo="
},
"quay.io": {
"auth": "azRjaDA6c3VwZXJzZWNyZXRwYXNzd29yZAo="
}
},
"HttpHeaders": {
"User-Agent": "Docker-Client/18.09.6 (linux)"
}
}
After a successful docker login command,
Docker stores a base64 encoded string from the concatenation of the username, a colon, and the password and associates this string to the registry the user is logging into:
$ echo azRjaDA6c3VwZXJzZWNyZXRwYXNzd29yZAo= | base64 -d -
luiscachog:supersecretpassword
A docker logout command removes the entry from the JSON file for the given registry:
$ docker logout quay.io
Remove login credentials for quay.io
$ cat ~/.docker/config.json
{
"auths": {
"https://index.docker.io/v1/": {
"auth": "azRjaDA6c3VwZXJzZWNyZXRwYXNzd29yZAo="
}
},
"HttpHeaders": {
"User-Agent": "Docker-Client/18.09.6 (linux)"
}
}
Docker Credential Helpers
Since docker version 1.11 implements support from an external credential store for registry authentication.
That means we can use a native keychain of the OS. Using an external store is more secure than storing on a “plain text” Docker configuration file.
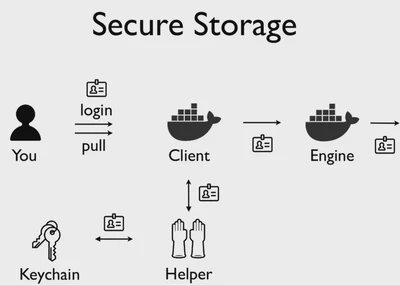
In order to use a external credential store, we need a program to interact with.
The actual list of “official” Docker Credential Helper is:
- docker-credential-osxkeychain: Provides a helper to use the OS X keychain as credentials store.
- docker-credential-secretservice: Provides a helper to use the D-Bus secret service as credentials store.
- docker-credential-wincred: Provides a helper to use Windows credentials manager as store.
- docker-credential-pass: Provides a helper to use pass as credentials store.
docker-credential-secret service
On this post we will explore the docker-credential-secretservice and how to configure it.
We need to download and install the helper. You can find the lastest release on https://github.com/docker/docker-credential-helpers/releases. Download it, extract it and make it executable.
wget https://github.com/docker/docker-credential-helpers/releases/download/v0.6.2/docker-credential-secretservice-v0.6.2-amd64.tar.gz tar -xf docker-credential-secretservice-v0.6.2-amd64.tar.gz chmod +x docker-credential-secretservice sudo mv docker-credential-secretservice /usr/local/bin/Then, we need to specify the credential store in the file
~/.docker/config.jsonto tell docker to use it. The value must be the one after the prefixdocker-credential-. In this case:{ "credsStore": "secretservice" }To facilite the configuration and do not make mistakes, you can run:
sed -i '0,/{/s/{/{\n\t"credsStore": "secretservice",/' ~/.docker/config.json
From now we are uning an external store, so if you are currently logged in, you must run docker logout to remove the credentials from the file and run docker login tostart using the new ones.
Let me know how this works for you.
References: